What Is Account Takeover Fraud?
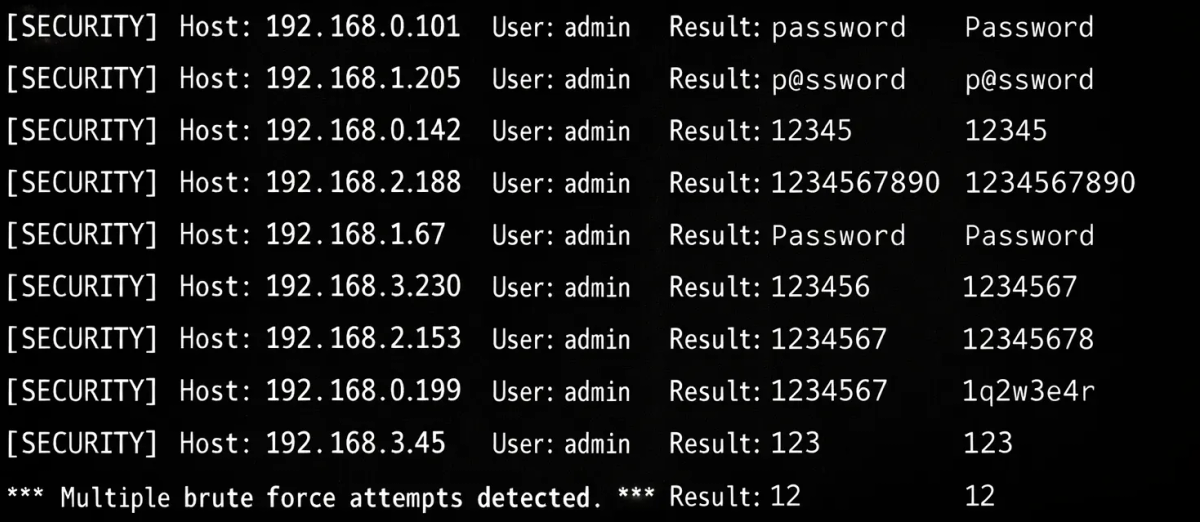
Account takeover fraud (ATO) is a cyberattack in which an unauthorized actor gains control of a legitimate user account. Instead of exploiting software vulnerabilities, attackers rely on stolen credentials, weak authentication controls, and automated bots to impersonate real users.
Once access is obtained, attackers can perform fraudulent transactions, steal personal or financial data, change account settings, or use compromised accounts to launch further attacks. Because the activity originates from valid accounts, it is often difficult to detect using traditional security controls.
With the rise of automation and credential leaks, account takeover fraud has become one of the most scalable and damaging forms of cybercrime.

Why Account Takeover Prevention Matters
Account takeover attacks create damage that compounds over time. Immediate financial losses from fraud, refunds, and chargebacks are often only the beginning.
Organizations also experience increased customer churn as users lose confidence in the platform’s security. Public disclosure of breaches amplifies reputational harm, especially in regulated industries. Legal and compliance penalties may follow if personal data is exposed or if controls are deemed insufficient.
Because compromised accounts can be reused for additional attacks, untreated ATO incidents often become recurring problems rather than one-time events.
Common Account Takeover Techniques
| Attack Type | What It Does | Primary Targets | Impact |
|---|---|---|---|
| Credential Stuffing | Tests leaked username/password pairs at scale using bots | Login pages, APIs | Mass account compromise, fraud |
| Brute Force Attacks | Tries many password combinations automatically | Weak-password accounts | Account lockouts, unauthorized access |
| Phishing | Tricks users into entering credentials on fake pages | End users | Credential theft, downstream ATO |
| Malware & Keylogging | Captures credentials from infected devices | Individual users | Silent, repeated compromise |
| Man-in-the-Middle (MitM) | Intercepts authentication traffic | Public networks | Session hijacking |
Account Takeover Prevention Controls and the Role of CAPTCHAs
Effective Account Takeover Prevention requires a layered defense strategy.
Strong password policies reduce weak credentials but cannot prevent credential reuse. Multi-factor authentication significantly reduces risk but does not stop bots from flooding login endpoints. Rate limiting helps slow brute force attacks but is ineffective against distributed bot networks. Behavioral monitoring detects anomalies but often reacts after compromise.
CAPTCHAs address a different and crucial stage of the attack lifecycle by stopping automated abuse before authentication logic is reached.
By distinguishing humans from bots, CAPTCHAs block automated login attempts, protect registration and password reset flows, and prevent large-scale credential stuffing campaigns. This early intervention reduces fraud, infrastructure load, and downstream remediation costs.
Traditional CAPTCHAs, however, introduce usability and privacy challenges. This is why modern CAPTCHA solutions are essential.
Why TrustCaptcha Is Ideal for Account Takeover Prevention
TrustCaptcha is designed specifically for modern Account Takeover Prevention, addressing both the technical and regulatory challenges of authentication security.
TrustCaptcha operates invisibly, introducing no puzzles or interruptions into the user journey. It is privacy-friendly by design, using no cookies or cross-site tracking mechanisms. Accessibility is built in, ensuring usability for all users without special accommodations.
Most importantly, TrustCaptcha stops bots before credentials are tested. By combining proof-of-work challenges with intelligent bot scoring, it neutralizes large-scale automation while preserving system resources and legitimate user access.
Best Practices for Account Takeover Prevention
To maximize effectiveness, TrustCaptcha should be deployed as part of a broader security strategy.
It works best when integrated into login pages, registration forms, password reset flows, and API authentication endpoints. Organizations should also enforce MFA for high-risk actions, monitor login anomalies, educate users about phishing, and secure APIs and mobile access points.
Together, these measures dramatically reduce the likelihood and impact of account takeover attacks.
Conclusion
Account Takeover Prevention is no longer optional. Today, it is a foundational requirement for secure digital operations. As attackers grow more automated and sophisticated, organizations must deploy defenses that scale just as effectively.
Modern CAPTCHA solutions like TrustCaptcha provide a powerful way to stop bots, protect user accounts, and preserve trust, without users even noticing.
👉 Try TrustCaptcha for free and see how modern CAPTCHA protection strengthens your Account Takeover Prevention strategy.