Understanding Brute Force Attacks and What They Typically Target
Brute force attacks remain one of the most persistent and damaging threats in modern cybersecurity. They are highly effective, especially against organizations with exposed authentication surfaces and inconsistent identity controls. At a practical level, a brute force attack is a trial-and-error method where automated tools repeatedly guess login credentials, encryption keys, or access tokens until something works.
For IT teams, the key point is that brute force rarely shows up as a single, obvious incident. It’s typically a sustained pressure campaign: scripted attempts, credential stuffing from breach dumps, and distributed botnets designed to evade basic IP blocks. This is why the modern objective isn’t merely to “block one attacker,” but to prevent brute force attacks by reducing the attacker’s ability to automate authentication attempts across your environment, without creating friction for legitimate users or overloading your support desk with lockouts.
In practice, brute force campaigns commonly target login forms and authentication endpoints, admin dashboards and CMS panels, API authentication, VPN and remote access gateways, and password reset / OTP verification endpoints. Any exposed authentication surface is a potential entry point, particularly when it can be hit repeatedly at scale, or when endpoint defenses are inconsistent across web, mobile, and API channels. As automation, AI-driven bots, and credential leaks grow, brute force techniques have become faster, cheaper, and harder to detect. This guide provides a complete overview of brute force attack types, how to recognize them, how to mitigate their impact, and most importantly how to prevent brute force attacks.
Different Types of Brute Force Attacks and How to Block Each One
Brute force isn’t one single technique. Attackers choose different styles depending on what they know, what they’ve stolen, and what defenses they expect. The table below breaks down common variants and the preventive countermeasures that work best.
| Attack Type | How It Works | What Attackers Typically Need | Typical Targets | Impact | Most Effective Countermeasures |
|---|---|---|---|---|---|
| Classic Brute Force | Tries large number of passwords automatically until one matches | Nothing | Login forms, admin panels | Breaks weak passwords; creates heavy auth load | Strong password policy, rate limiting, Captcha, lockout thresholds |
| Dictionary Guessing | Uses common password lists and wordlists (often with leaked “top passwords”) | A password list; sometimes known usernames | Consumer logins, CMS, SaaS portals | Fast compromise of predictable passwords | Strong password rules, banned password lists, Captcha, MFA |
| Hybrid Guessing | Combines dictionary words with patterns | Wordlists + common patterns | Enterprise portals, SSO login pages | Defeats “semi-strong” human passwords | Password managers, random passphrases, Captcha, MFA |
| Password Spraying | Tries a small set of popular passwords across many accounts to avoid lockouts | A list of usernames | SSO, email, corporate apps | Slow but scalable; compromises multiple accounts | Captcha, MFA, anomaly detection, per-account and per-IP throttling |
| Credential Stuffing | Reuses breached username/password pairs across multiple sites | Credential dumps from breaches | E-commerce, login | High success rate if users reuse passwords | Captcha, MFA, breached-password checks |
| Reverse Brute Force | Uses one known password against many usernames (e.g., “Welcome123!”) | A likely password | Employee portals, legacy systems | Can compromise multiple users quickly | Captcha, MFA, password hygiene, monitoring |
| Distributed Brute Force (Botnets) | Spreads attempts across many IPs/devices to evade IP-based blocks | Botnet capacity | High-value targets | Evades simple IP blocking; sustained pressure | Proof-of-work CAPTCHA (TrustCaptcha), behavioral scoring, adaptive throttling |
| Session/Token Guessing | Attempts to guess or brute weak tokens, session IDs, or API keys | Knowledge of token formats or weak entropy | APIs, session endpoints | Account takeover without passwords | Strong token generation, rotation, rate limiting, Captcha, Token lifetime |
| Password Reset Abuse | Attacks reset flows to discover valid accounts or brute OTP codes | Endpoint access; sometimes leaked emails | Reset + OTP verification endpoints | Account enumeration, takeover attempts, support overload | Captcha, rate limits, OTP hardening, anti-enumeration messaging |
Indicators of Brute Force Attacks
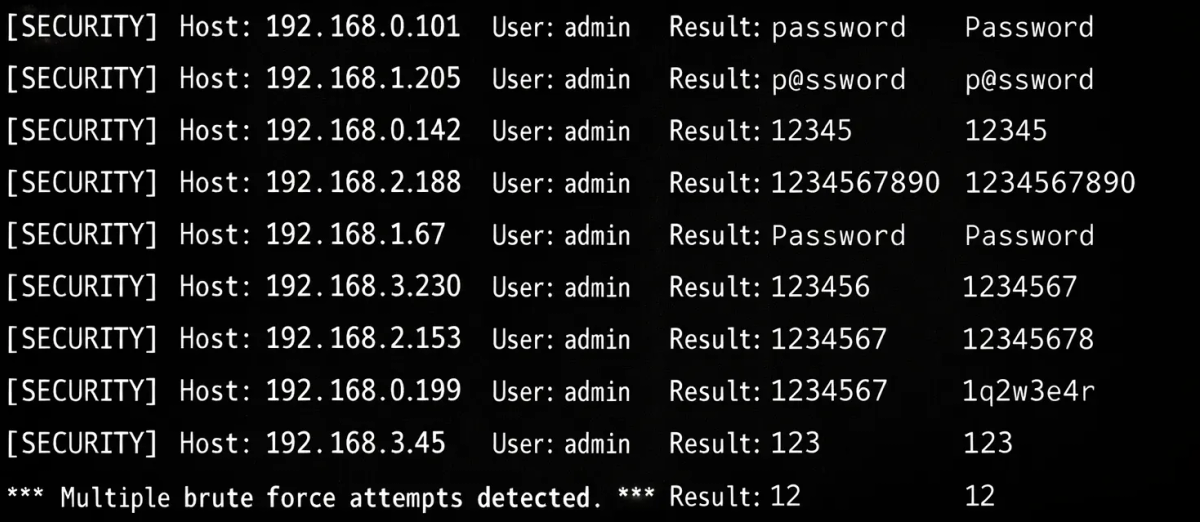
If you’re seeing abnormal authentication behavior, then you’re likely dealing with an automated attempt against your authentication surfaces.
To identify a brute force attempt, look for patterns that indicate automation rather than user error:
- A spike in logins clustered around a small set of accounts with many of them failing.
- Attempts spread across many accounts with the same password guess.
- Repeated login requests with rotating IPs or unusual geographies.
What to if you suspect a brute force attack
When a brute force attack is in progress, speed matters. The objective is to reduce automation capacity quickly while avoiding broad lockouts that create business disruption.
Recommended immediate actions:
- Protect the endpoint right away with a CAPTCHA to stop automation.
- Throttle requests on auth, reset, and OTP endpoints (IP/user-based).
- Enable MFA (or enforce step-up authentication) for high-risk logins.
- If necessary, temporarily lock or step-up protect targeted accounts.
- Force password resets for accounts showing signs of compromise.
- Review logs and alerts for successful logins from suspicious locations or devices.
How to Prevent Brute Force Attacks (Layered Strategy)
There’s no single solution to prevent all types of brute force attacks. The most sustainable prevention is a layered use of multiple measures:
- Strong password policies (length, uniqueness, banned password lists)
- CAPTCHA-based bot protection to stop automated attacks
- Multi-factor authentication (MFA) for account takeover resistance
- Monitoring and alerting for anomalies on auth endpoints
- Rate limiting and throttling to reduce high-frequency attempts
CAPTCHAs help because they target the biggest advantage attackers have: automation. Without automation, brute force becomes slow, inefficient, and expensive. A modern CAPTCHA also reduces downstream costs: fewer authentication-related incidents, fewer password reset events triggered by bots, and less unnecessary load on identity systems.
How CAPTCHAs Help Prevent Brute Force Attacks
Modern CAPTCHAs are especially effective at mitigating automated brute force attacks by adding a human and technical verification layer before your application accepts the request. In practice, they help because:
- They prevent bots from repeatedly submitting login forms at high speed.
- They disrupt automated tooling cycling through password lists and credential dumps.
- They break pattern-based login attempts that rely on predictable, repeatable requests.
- They slow attackers down by forcing additional work for every attempt.
- They reduce both burst attacks and “low-and-slow” attacks that try to avoid detection.
When used alongside safeguards like MFA and monitoring, a CAPTCHA becomes a core line of defense that makes brute force attacks inefficient and far easier to contain, without forcing heavy-handed controls that impact legitimate users.
Introducing TrustCaptcha: A Modern CAPTCHA for Brute Force Defense
TrustCaptcha is a next-generation CAPTCHA designed for organizations that need strong security without sacrificing privacy, accessibility, or conversion. It runs invisibly in the background and focuses on stopping automation where it matters most: on authentication and verification endpoints.
How TrustCaptcha Prevents Brute Force Attacks (Proof of Work + Bot Score)
TrustCaptcha prevents brute force attacks using two mechanisms that directly undermine automated guessing and distributed bot traffic.
Proof of Work (PoW):
TrustCaptcha uses proof-of-work to require a small computational task per request. For real users, this happens quickly and invisibly. For bots operating at scale, it changes the economics:
- Every attempt consumes compute.
- High-volume attacks become slower by design.
- Distributed botnets pay per request.
- The attacker’s “cheap guessing” turns into expensive, throttled guessing.
In brute force terms, PoW scales against automated abuse without blocking normal users. This is especially valuable for high-traffic environments where you can’t rely solely on lockouts or IP blocks without collateral damage.
Bot Score:
TrustCaptcha also assigns a bot score by analyzing request context and behavior. The benefit is a smarter control plane:
- Low-risk traffic passes smoothly.
- Suspicious patterns and attacks take longer and are more expensive for attackers.
- Malicious automation gets slowed or blocked.
This risk-based approach is especially useful for brute force scenarios where attackers rotate IPs, mimic browsers, and attempt to blend into real traffic. Instead of relying on brittle allow/block rules, TrustCaptcha adapts to the risk level, supporting a stronger security while maintaining high conversion and accessibility.
Conclusion
Brute force attacks are a common threat. They are usually automated and frequently aimed at the exact endpoints every application depends on: login, reset, OTP, and API auth. The good news is that organisations can build layered defenses and break attacker automation early.
Modern CAPTCHA protection remains one of the most effective ways to stop brute force attempts at the source. With proof-of-work and bot scoring, TrustCaptcha makes automated guessing expensive, slow, and far less likely to succeed, without legitimate users even noticing.
👉 Try TrustCaptcha for free and see how it works in your own environment.